Hacktivists and western cybersecurity groups, who played a vital role in helping Ukraine in their fight against Russian cyberattacks, appear to be reenacting their exploits in service of Iranian protesters to defeat governmental restrictions and censorship.
A group called, Black Reward, hacked email system of Iran’s nuclear establishment and threatened to publish sensitive documents in an attempt to draw attention to protests that erupted over the death of Mahsa Amini who died after being taken into custody for not observing the country’s strict dress code. Iran’s Atomic Energy Organisation confirmed the hacking, by a “foreign country,” of an email server of its subsidiary, the Atomic Energy Production and Development Company.
The group demanded on October 22 release of those arrested for protests and other political prisoners. Following the expiry of their 24-hour deadline, the hackers published some of these email attachments on Telegram.
“The published documents contain the contracts of Iran Atomic Energy Production and Development Company with domestic and foreign partners, management and operational schedules of Bushehr power plant, identity details and paystub of engineers and employees of the company as well as passports and visas of Iranian and Russian specialists of Bushehr power plant,” stated the group on social media.
The hacktivists have also warned that “unlike Westerners, we do not flirt with criminal clerics, and if we promise something, we fulfil it 100%.”
The Black Reward further said that it has retrieved a total of 50 GB of data, including over 100,000 email messages and more documents would be released in the coming days. Earlier last week, the group has announced its hacking of emails of managers and employees of Press TV, the government’s international English news channel. The group’s Twitter bio claims the group is part of the Iranian hacker community but is opposed to the nation’s theocratic government, which it calls criminals.
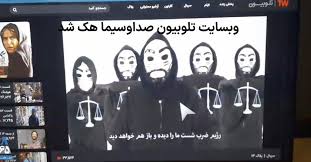
Earlier on October 9, Iran’s state-run television was hacked by protesters during a live broadcast, disrupting coverage to display an anti-government message. During the evening news bulletin, the Islamic Republic of Iran Broadcasting Programme was cut off to a black screen showing a mask, before transitioning to a gun targeting Supreme Leaders Ali Khamenei’s face with flames surrounding him. Below him were images of four Iranian women who Iranian police have accused of killing. Hacktivist group, Edaalate Ali (Ali’s Justice) has claimed responsibility.
Last month, several Iranian government and state-affiliated media websites were hacked and brought down several times in support of the of the protesters. Hackers of the well-known “Anonymous” group, who also played a major role in favour of Ukraine, claimed responsibility for the attacks on Iranian sites, which include “smart services” website of the government.
Anonymous and other global hacking groups, including thousands of amateur ones, are organizing online to orchestrate cyberattacks on Iranian officials and institutions, as well as share tips on how to get around curbs on internet access by using privacy-enhancing tools.
According to Check Point Research (CPR), the hackers are helping the protesters to bypass the restrictions and censorship to communicate with each other. “CPR sees the sharing of open VPN servers to bypass censorship and reports on the internet status in Iran, as well as the hacking of conversations and guides,” according to a report shared with Insfosecurity magazine. Some of these Telegram groups include the `Official Atlas Intelligence Group’, counting over 900 members, `ARVIN’, which has about 5000 followers, and `Red Blue’, a channel with about 4000 members.
Meanwhile, the U.S. government has sanctioned Iranian cybersecurity and hacking school, Ravin Academy, and its co-founders, Seyed Mojtaba Mostafavi and Farzin Karimi, who are said to be members of Iran’s intelligence ministry. The Washington Post also reported on October 27 that the Treasury Department sanctioned another Iranian firm, Samane Gostar Sahab Pardaz Private Limited Company, which it said is one of Iran’s “main operators of social media filtering services.” These are the latest batch of sanctions targeting internet and cybersecurity-related Iranian firms and people in the wake of protests following the death of Mahsa Amini.
The Treasury Department has also sanctioned earlier this month Iranian Communications Minister Eisa Zarepour and Iranian Cyber Police head Vahid Mohammad Naser Majid for their alleged roles in blocking internet service and monitoring internet users. Iranian authorities have restricted internet service and cut off access to some major U.S. social network apps as part of measures to quell the protests.